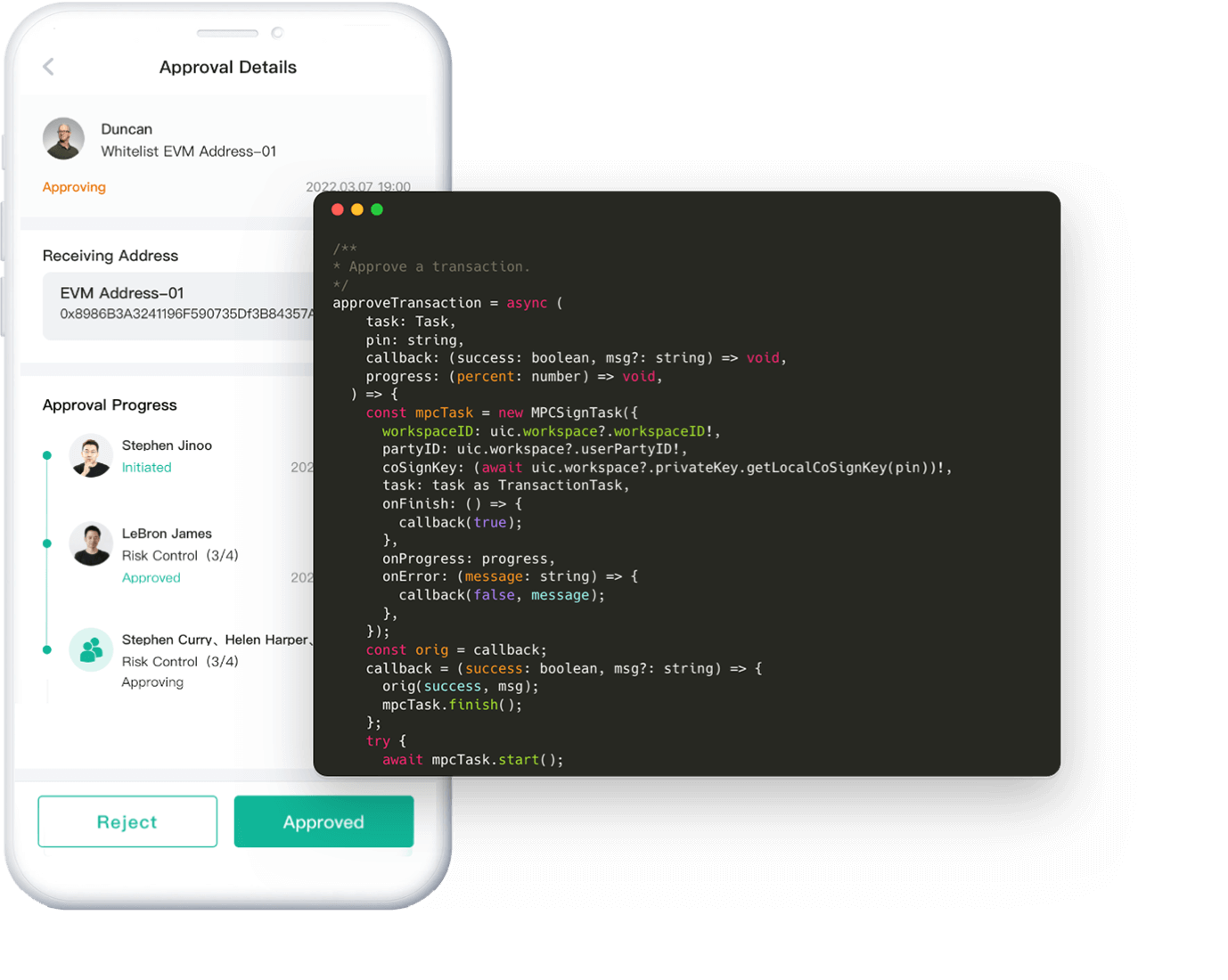
Cryptographic Infrastructure Library
We created the Safeheron Cryptography Basic Algorithm Library suite in C++ to make it easier to develop upper-layer cryptographic protocols, which includes the Big Number Computation Library, the Abstract Elliptic Curve Algorithm Library, the Homomorphic Encryption Algorithm Library, the Secret Sharing Scheme Algorithm Library, and the Zero-Knowledge Proof Protocol Algorithm Library.
Check out our code on Github