100% Asset Control
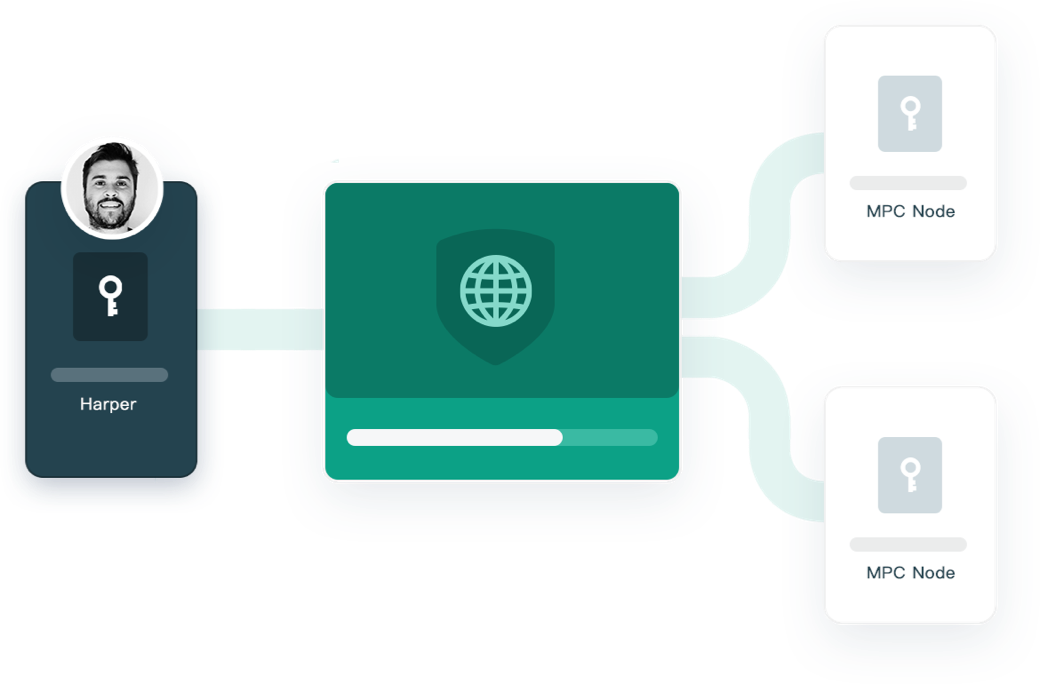
MPC Privacy Network for Private Key
Safeheron's proprietary MPC cryptography utilizes key shards to compute signatures without exposing the private key and shards to any third party, protecting the single private key from external hackers and malicious insiders.
Check out our code on GitHub